Single Sign-On (SSO) does more than save passwords. In an induction platform that governs access to policies, assessments and compliance evidence, SSO becomes a control point for security, accountability and operational clarity. Lets go over some practical reasons why companies should enable SSO with INDUCT FOR WORK, the risks it removes and the governance advantages it delivers across IT, Safety/WHS and HR.
1) Stronger security by default
One identity, centrally governed. With SSO, user authentication is handled by your identity provider (IdP), so password rules, MFA, device posture checks and conditional access policies apply the moment someone attempts to open INDUCT FOR WORK.
Reduced password sprawl and phishing. Users no longer maintain a separate username/password for the induction system. Fewer credentials mean fewer attack surfaces and less chance of weak or reused passwords.
Instant revocation. Disable a user once in the IdP and their access to INDUCT FOR WORK stops immediately. That closes a common gap where departed employees retain access to systems that hold personal data and compliance records.
2) Clean, auditable access for compliance
Provable user identity. Every completion, acknowledgement and uploaded licence ties back to an enterprise-verified identity. During audits (ISO 27001, client due diligence, regulator inquiries) this linkage reduces debate about who completed what and when.
Consistent MFA posture. Enforcing MFA at the IdP level ensures INDUCT FOR WORK benefits from the same second factor as email, HRIS or finance systems—no special exceptions, no weaker links.
Least-privilege administration. Role mapping from your IdP groups (e.g., safety_admins, contractor_managers) helps you assign exactly the right administrative level within the platform and keep a defensible separation of duties.
3) Better joiner–mover–leaver hygiene
Joiners: New employees or contractors can be granted access through existing groups in the IdP, eliminating manual account creation in online induction platform and the risk of typos or duplicates.
Movers: When someone changes teams or sites, their IdP group membership changes; their INDUCT FOR WORK access follows suit, ensuring they see the right role- or site-specific modules only.
Leavers: Terminations in HR or IT feed into the IdP, which then cascades to connected apps. Access to induction records ends at the same time as everything else—no lingering exposure.
4) Simpler user experience (and fewer helpdesk tickets)
One click, familiar prompt. Users authenticate with the same sign-in screen they already trust. That removes the “what’s my password for the induction site?” cycle and shrinks password reset volume.
Faster completions. When access is frictionless, more people complete their modules before arriving on site. That lifts “completion before arrival” rates and reduces reception or gate delays.
5) Segmentation and policy control across sites
Group-based targeting. Use IdP groups (e.g., “Melbourne-Contractors”, “Warehouse-Visitors”, “Event-Day-Staff”) to assign the correct induction streams in bulk. By anchoring targeting to the IdP, you keep content audiences consistent with your organisation chart and vendor onboarding rules.
Conditional access for higher-risk roles. If your IdP supports device compliance checks or geofencing, you can require a compliant device + MFA for users accessing high-risk modules (e.g., working at heights, hot work).

6) Governance that stands up to scrutiny
Unified logs. Authentication attempts and session details are logged at the IdP, while completions and acknowledgements are logged in INDUCT FOR WORK. Together they form a robust audit trail—who signed in, when, from where and what was completed.
Policy alignment. Security and WHS policies often require MFA, password rotation and timely deprovisioning. Enabling SSO demonstrates technical enforcement, not just a paper policy.
7) Practical architecture notes
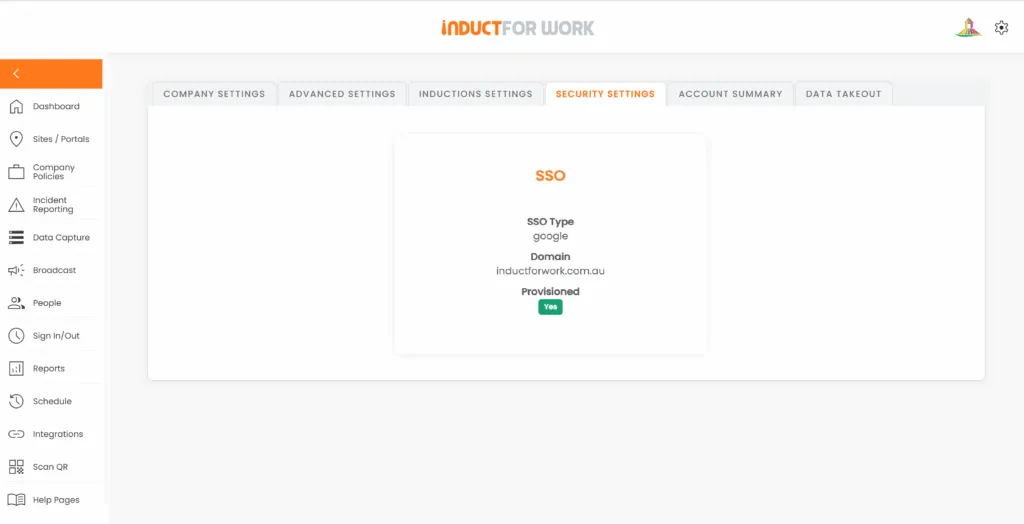
Protocols. Most organisations standardise on SAML 2.0 or OpenID Connect (OIDC) for SSO. INDUCT FOR WORK supports standards-based SSO; choose the protocol that aligns with your IdP (e.g., Azure AD/Microsoft Entra ID, Google Workspace, ADFS).
Group/role mapping. Create or reuse IdP groups (e.g.,
ifw.admin,ifw.manager,ifw.user) and map them to roles inside the platform. This avoids one-off permissions and makes audits straightforward.User lifecycle. If you use automated provisioning (e.g., SCIM in your IdP), keep the source of truth in HR/IT. Even without SCIM, SSO plus group-based access delivers most lifecycle benefits with minimal overhead.
Environments. Test SSO in a staging or pilot environment first, then roll to production with a small cohort before full deployment.
8) WHS and operational wins beyond IT
Gate readiness. Faster sign-in means workers reach their modules sooner; managers can verify induction status with QR checks or reports, rather than troubleshooting credentials.
Data minimisation. With SSO, you don’t need to store standalone passwords in the induction platform. Reducing stored secrets is good security hygiene and simplifies breach response planning.
Confidence for clients. When bidding or passing client audits, being able to state “access to our induction and compliance platform is SSO-protected with MFA and central off-boarding” is a tangible differentiator.
9) Setup checklist (15–30 minutes per environment)
Confirm protocol: SAML 2.0 or OIDC.
Create enterprise app: Add INDUCT FOR WORK in your IdP; note the ACS/redirect URLs and entity/client IDs.
Upload metadata / secret: Exchange SAML metadata or OIDC client credentials as required.
Map attributes/claims: Pass a unique identifier (UPN/email), display name and group claims needed for role mapping.
Assign groups/users: Start with a pilot group.
Test flows: Sign-in, first-time access, role mapping, error handling and a leaver scenario.
Rollout: Communicate to users; update your access policy and IT runbook.
10) Frequently asked questions
Will SSO lock out external contractors?
No. You can federate through their company IdP (if they have one) or keep a controlled exception path. Aim to minimise exceptions and time-limit them.
Do we still need MFA if we have SSO?
Yes—MFA should be enforced at the IdP level. That way every SSO-protected app, including INDUCT FOR WORK, inherits the same strong factor.
What happens if the IdP is unavailable?
Follow your business continuity plan. Most IdPs offer strong uptime SLAs; you can also keep a small, controlled break-glass admin path with strict monitoring.
Enabling SSO for INDUCT FOR WORK strengthens your security posture, simplifies life for users and gives Safety and HR cleaner evidence when it counts. You get immediate wins, fewer resets, faster completions, instant off-boarding and long-term governance advantages that align with audit and client expectations. If you haven’t switched it on yet, make SSO your next change (available on Ultra plus package): it’s a modest configuration task with outsized benefits for compliance, operations and trust.